No results found
We couldn't find anything using that term, please try searching for something else.
This toolbox category contains 8698 tools
Document

Urban VPN Proxy
Get the best secured Free VPN access to any website, and unblock content with Urban VPNProtect your online identity, stay protected & hide your IP with Urban Free VPN Proxy for Chrome! Urban VPN Free proxy servers are available in…

Urban VPN Proxy
Urban VPN Proxy best secured Free VPN access website , unblock content Urban VPN Urban VPN Proxy is available to install from Chrome Web Store and for download from this page. It has 4,000,000+ active users The latest version is…

Edit and Clone IPsec VPN profiles
Edit and Clone IPsec VPN profiles You is edit edit clone custom IPsec VPN profile . edit clone VPN profile migrated earlier release , you is need need select VPN topology VPN profile . Note: You cannot modify or delete…

Best VPNs of 2024: Top 4 VPN services, tested and reviewed
How we tested Making this guide to the best VPNs involved hands-on testing, which I'll describe in more detail shortly, but it also hinged heavily on guidance from cybersecurity experts. When it comes to the types of things consumers should…

The Best VPN Extensions for Chrome in 2024
Most VPN services provide apps for just about every platform, and many provide extensions for Google's Chrome browser. However, not all these extensions are as powerful as their sibling apps, and almost none of them work the same as true…
![5 Best VPN Extensions for Edge [Meticulously Tested]](/img/20241112/WyK67H.jpg)
5 Best VPN Extensions for Edge [Meticulously Tested]
No browser is a hundred percent safe and you should take extra security measures to keep your information intact. That’s why a VPN is recommended when browsing the web. Today we’ll take a look at the best VPN extensions for…

Configure a VPN client for P2S RADIUS: other authentication methods
Configure a VPN client for point-to-site: RADIUS - other methods and protocols Article03/12/2024 In this article To connect to a virtual network over point-to-site (P2S), you need to configure the client device that you'll connect from. This article helps you…
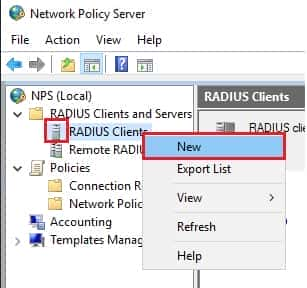
How to configure Windows Server and UDM-PRO UniFi Controller for RADIUS VPN access
In this tutorial you will be shown how to configure Windows Server and UDM-PRO UniFi Controller for RADIUS VPN access. Why is this useful? Well this allows us to just disable a user account in Active Directory after a termination…
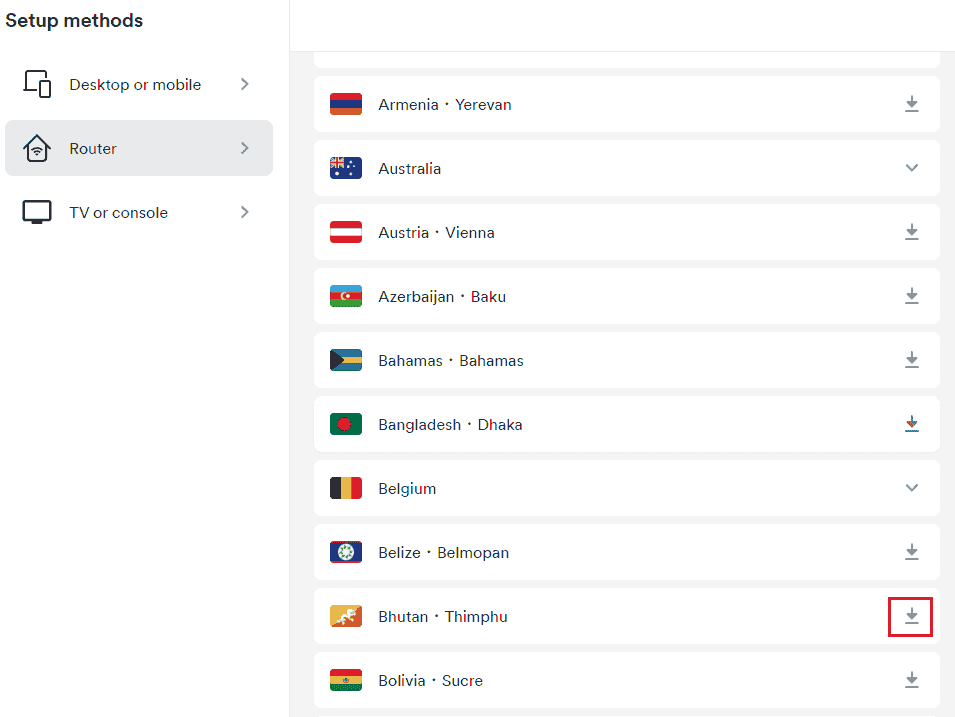
How to set up Surfshark VPN on an AsusWRT router
In this tutorial, you will learn how to configure the Surfshark VPN tunnel on your AsusWRT router.To proceed, you need a router with AsusWRT firmware and an active Surfshark subscription. You can find the available plans on Surfshark’s pricing page.…
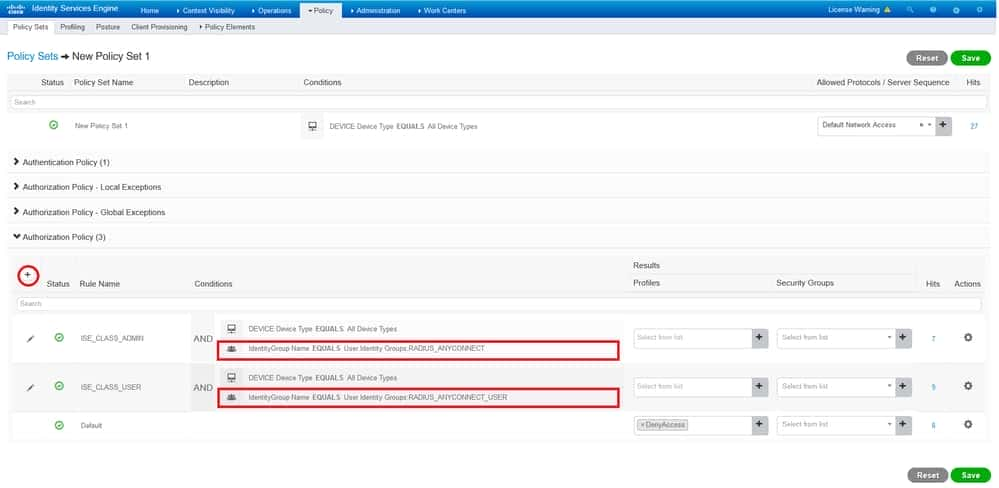
Configure Remote Access VPN with RADIUS Authentication on ISE and Group-Policy Mapping
IntroductionThis document describes configuring Remote Access VPN for group-policy mapping with Cisco Identity Services Engine (ISE).PrerequisitesRequirementsCisco is recommends recommends knowledge topics : Cisco Secure Client (AnyConnect) Cisco ISE Remote Access VPN Cisco Adaptive Security Appliance ( ASA ) Components usedThe…
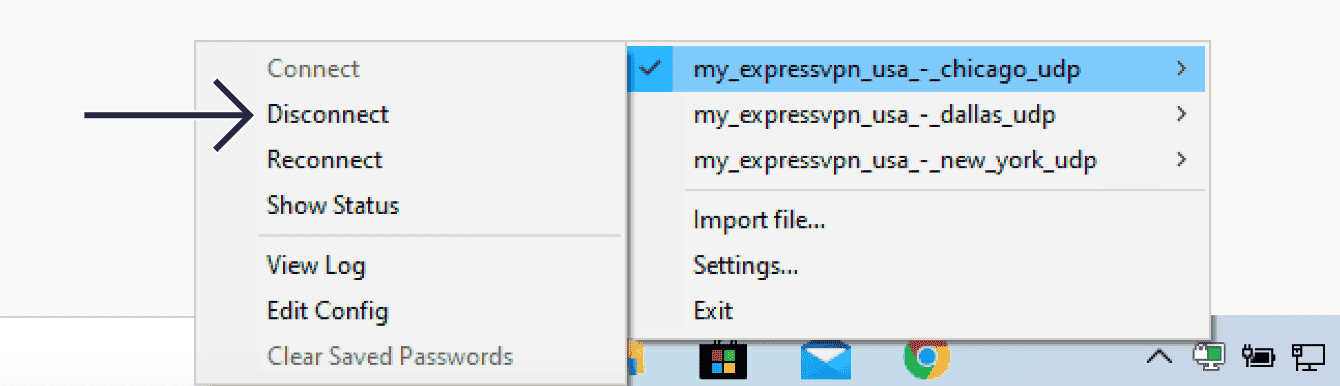
Set Up OpenVPN on Windows XP, Vista, 7, 8 and 10
Last updated: March 25, 2024This tutorial will show you how to set up ExpressVPN on Windows using the OpenVPN GUI (graphical user interface).The OpenVPN GUI is a free graphical frontend for running the OpenVPN protocol on Windows XP, Windows Vista,…
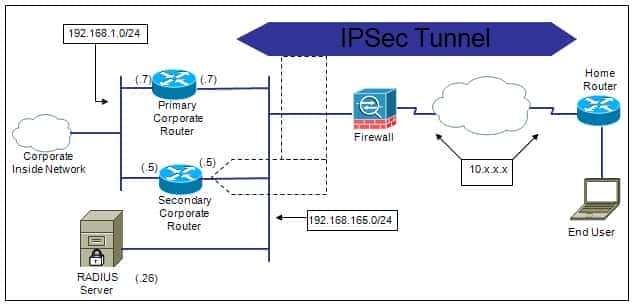
Exploring Remote Access VPN (Easy VPN) on Cisco Router with Cisco Secure ACS 5.x
Introduction There are times when you want your employees to have a secure access to your corporate network resources through your Cisco router, along with the option to centrally manage their access with easy manageable configuration rollout on Cisco routers.…

Technical Tip: FortiGate Site-to-Site VPN with Str…
Logical Topology for Site-to-Site VPN between FortiGate and Strongswan in Ubuntu Server 20.04: Ubuntu 20.04 Public IP ens9: 10.191.20.247/20Private IP ens10: 192.168.100.1/24 installing Ubuntu server , it is is necessary set IP addresses Setup an IP address on Ubuntu…
How to Setup OpenVPN on TP-Link Routers (Windows)
OpenVPN is a free VPN (virtual private network) service that allows you to remotely access your Home network from anywhere with an open internet service. OpenVPN is a multiplatform service that works with both Android and iOS operating systems, allowing…
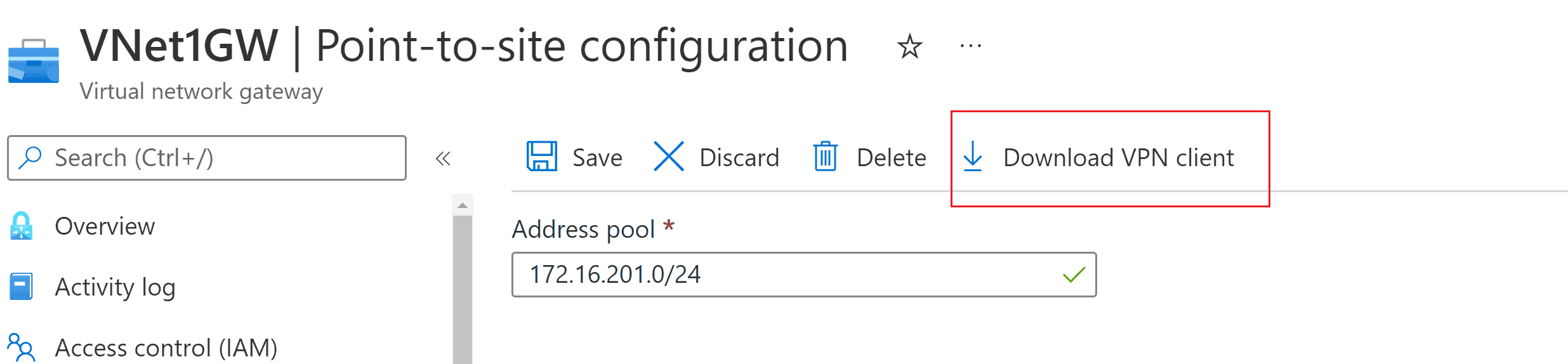
P2S VPN client profile configuration files
Generate VPN Client profile configuration files - Microsoft Entra ID authentication Article05/15/2024 In this article This article helps you generate and extract VPN client profile configuration files. Client profile configuration files contain information that's used to configure your VPN client.…

Get started with AWS Client VPN
Get started with AWS Client VPNtutorial , you is create create AWS Client VPN endpoint following : Provides all clients with access to a single VPC. Provides all clients with access to the internet. Uses mutual authentication . The following…
